Install device certificate palo alto – Installing device certificates on Palo Alto firewalls is a crucial step for securing network communication and ensuring device authenticity. This comprehensive guide will provide a detailed overview of the process, from understanding the benefits and types of device certificates to the steps involved in installation, verification, and troubleshooting.
Device certificates play a vital role in establishing trust between devices and network infrastructure. They provide a secure way to authenticate devices and encrypt data, enhancing the overall security posture of an organization.
Device Certificate Installation Overview
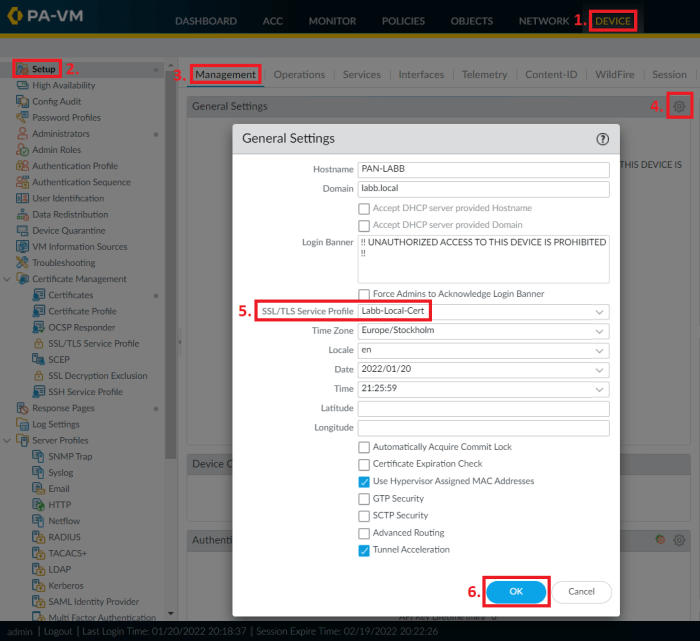
Installing device certificates on Palo Alto firewalls enhances security by authenticating the device and enabling secure communication. It allows the firewall to establish trust with other devices and services, ensuring data integrity and confidentiality.
There are two main types of device certificates: self-signed certificates, which are created and signed by the device itself, and certificates issued by a Certificate Authority (CA), which are considered more trustworthy and secure.
Certificate Authority (CA) Setup
To issue device certificates, it is necessary to create a CA. A CA is a trusted entity that validates the identity of devices and issues certificates to them. Setting up a CA involves generating a root certificate and creating a certificate signing request (CSR) for each device.
Using a trusted CA is crucial for certificate validity and security. Trusted CAs are recognized by browsers and other applications, ensuring that certificates issued by them are accepted and trusted.
Certificate Installation on Palo Alto Firewall: Install Device Certificate Palo Alto

Installing a device certificate on a Palo Alto firewall involves importing the certificate into the firewall’s management interface. This can be done through the CLI or web interface. The CLI method provides a more granular level of control, while the web interface offers a user-friendly experience.
Once the certificate is imported, it needs to be bound to a specific interface or service. This ensures that the certificate is used for authenticating the correct traffic.
Certificate Verification and Troubleshooting

Verifying the installation and validity of a device certificate is essential to ensure its effectiveness. This can be done by checking the certificate details in the firewall’s management interface or using external tools like OpenSSL.
Common certificate-related issues include certificate expiration, revocation, and untrusted CAs. Troubleshooting these issues typically involves renewing the certificate, revoking it, or adding the CA to the firewall’s list of trusted CAs.
Best Practices for Device Certificate Management
Proper management of device certificates is crucial for maintaining security and compliance. Best practices include:
- Regularly renewing certificates before they expire.
- Revoking certificates that are no longer in use.
- Backing up certificates in a secure location.
- Maintaining a central repository for certificate management.
- Following industry standards and regulations for certificate security.
Expert Answers
What are the benefits of installing device certificates on Palo Alto firewalls?
Device certificates provide several benefits, including enhanced security, improved device authentication, encrypted communication, and compliance with industry standards.
What are the different types of device certificates that can be installed?
There are various types of device certificates, including self-signed certificates, third-party certificates, and certificates issued by a Certificate Authority (CA).
How do I install a device certificate on a Palo Alto firewall?
Installing a device certificate on a Palo Alto firewall involves generating a certificate signing request (CSR), obtaining a signed certificate from a CA, and importing the certificate into the firewall.
